With the release of Gen10 series earlier this year, most of the people were focusing on the new Skylake processors and other performance and scalability enhancements.
However, one of the most important new features in Gen10 are the changes on security level. HPE is raising the security bar enormously here… They even state that Gen10 is currently the most secure server in the world. So, is this true? And why? And how does it work? Read further…
Security in the Gen10 portfolio is checked and guaranteed on 3 levels: Protect, Detect and Recover.

Protect
By implementing Silicon based Root of Trust, HPE is embedding its validation signature in the ASIC which means that they are burned into the ASIC in the fab. The fab is completed before the server even goes into production. Thus, the HPE silicon root of trust protects the server from any firmware attacks all the way through production, shipping, distribution, and the entire supply chain process. Read this and this article to show the importance about securing your supply chain.
Also important is the security level on supply chain level, since HPE builds the fab and the firmware… No dependency on other OEM’s or ODM’s (Original Design Manufacturer) whatsoever…
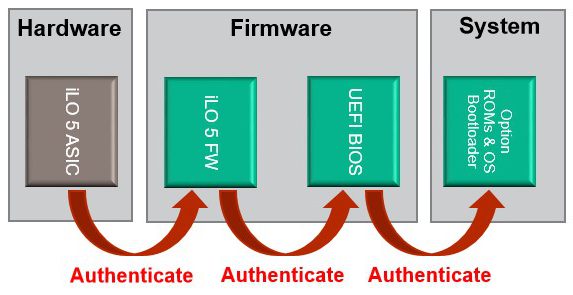
When the server is connected to power, HPE-designed logic in iLO chip validates the iLO firmware.
Only if the authentication is successful (being the iLO firmware being ‘safe’), iLO firmware then validates the System ROM. The digital signature must match or the ROM is not executed. Since iLO firmware is trusted, now the ROM is trusted (Chain of Trust).
The UEFI ROM then validates Option ROMs and the OS Bootloader via UEFI Secure Boot. Option ROMs and OS Bootloader are NOT executed if they fail authentication.
Result: the root of trust is initiated and secured by the silicon/FAB which proves the Silicon root of trust.
Detect
Like a virus scanner in the operating system, HPE implemented a ‘firmware scanner’ in the hardware, scanning the 5 firmware’s running on every server motherboard (iLO, UEFI, CPLD, IE and ME) every day for vulnerabilities, checking its digital fingerprint with the one stored in the silicon/fab.
Alert of compromised code will be send to the administrator through iLO audit logs and email.
There is also an additional option available for physical (chassis) intrusion detection.
Recover
If compromised code is detected, manual or automatic recovery will be the options to a known good state. The options are there to recover to factory settings or last know good or not recovering at all taking the server off-line for root cause analysis.
This recovery is available for all 5 running firmware’s on the server. Unique in the server market.
Combining all this makes the Gen10 hardware the most secure server in the world today. It is also the first server being FIPS140-2 and CNSA compliant on the market today.
My take:
Why is firmware protection important, I hear you say? More important than you can imagine. Just look what happened last year on October 21st. The Mirai Botnet was able to ‘bring down the internet’, or at least some important big websites like Twitter, Amazon, Netflix and so on. Root cause analysis has shown that DNS servers were attacked (I called it more overloaded than attacked, that’s what news sites make from it) by IoT devices like IP camera’s, printers and smart TV’s. These were all running compromised firmware… And no one did see it…
So yes, firmware attacks and IoT is the new big threat in IT. And we should take this serious.
Great job from HPE, changing the server discussion from just quickspecs and features to a new kind of discussion being hardware security… To be continued for sure!
Be social and share!
